Vault Key Backup and Restore
CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. key material is shared across the CORE and the participants while its management data is stored in the CASP
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. key material is shared across the CORE and the participants while its management data is stored in the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. DB. The backup of this data is divided into steps done during setup and steps needed in an ongoing basis. The backup data is used for recovery.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. DB. The backup of this data is divided into steps done during setup and steps needed in an ongoing basis. The backup data is used for recovery.
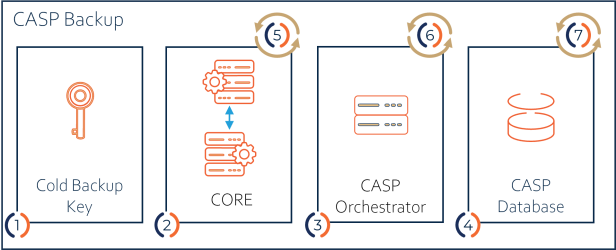
The numbers in the figure correspond to the respective steps in the next section.
Backup
Setup Tasks for Backup
During setup, perform these tasks:
-
Create RSA keys that will be used to encrypt and decrypt the backup of CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vault key.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vault key. The vault key backup is applied to recover CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vault key from a loss of the entire system. See Prepare Vault Key Recovery.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vault key from a loss of the entire system. See Prepare Vault Key Recovery. -
Setup the CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vault key backup encryption.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vault key backup encryption. The public RSA keys are installed on CORE. See Setup CORE.
-
Create a CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. quorum
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. quorum One or more groups, comprised of participants with redundancy.
One or more groups, comprised of participants with redundancy.
Your quorum
 One or more groups, comprised of participants groups should have more participants than the required minimum number for approval. This setup allows replacing a participant
One or more groups, comprised of participants groups should have more participants than the required minimum number for approval. This setup allows replacing a participant A member of any of the quorum groups., which may be necessary if someone loses their phone or leaves the company. For example, your group has 3 participants required for approvals, and it has 4 participants. A participant
A member of any of the quorum groups., which may be necessary if someone loses their phone or leaves the company. For example, your group has 3 participants required for approvals, and it has 4 participants. A participant A member of any of the quorum groups. loses his phone, and the remaining 3 can reactivate the participant
A member of any of the quorum groups. loses his phone, and the remaining 3 can reactivate the participant A member of any of the quorum groups. on a new phone.
A member of any of the quorum groups. on a new phone.Consider creating a couple of bots that are used as participants. These bots can be safely stored and only used when needed to meet the minimum quorum
 One or more groups, comprised of participants for approval.
One or more groups, comprised of participants for approval. -
Setup the CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. database backup.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. database backup.Use the methods described by each database vendor for backup of your CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. DB:
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. DB:It can be helpful to save a copy of your casp.conf configuration file.
Ongoing Backup Tasks
The following are ongoing backup tasks to execute periodically:
-
Backup the vault key.
You should backup the vault key immediately upon creation of the vault.
Note:
-
For BIP32 vaults, it backs up the first key that was derived normally on the derivation chain. For example:
-
For the chain
m/0'/1'/2/3/4- it backs up only the2key. -
For the chain
m/1/2/3/4- it backs up only the1key. -
For BIP44 vaults, it backs up only the account key.
-
- For a deterministic
 Calculation that each time results in the same value (non-hierarchical) vault use:
Calculation that each time results in the same value (non-hierarchical) vault use:https://<casp-server>/api/v1.0/mng/vaults/{id}/backup
- For BIP32 use:
https://<casp-server>/api/v1.0/mng/vaults/{vaultId}/backup/{publicKey}
- For BIP44 use:
https://<casp-server>/api/v1.0/mng/vaults/{id}/coins/{coin-number}/accounts/{account-number}/backup
Replace
{coin-number}with the number for the coin type that you are using. You can see a list here.
Replace{account-number}with your account number. You need to call this command once for each account number.Note
This is the backup of the account root key, not the actual key that holds the currency. All other account addresses can be derived from this key. -
Backup the CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. database.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. database.
Use the methods described by each database vendor for periodic backups of your CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. DB:
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. DB: -
Backup the CORE.
Use the APIs found in the CASP API descriptions:
To retrieve the backup data, use one of the following API requests:
The returned JSON includes encrypted vault key and metadata required for its restoration. Save the returned JSON to a file for use in the verify/restore process.
Warning
Segregate a backup file from the keys required to decrypt the file's material.
Backup CORE periodically. Use the CORE procedures, which can be found in the CORE User Guide.
Recovery Scenarios
The following sections present different recovery scenarios and what is required to restore functionality.
CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. provides the Status API that returns the health of the components. You can run this command to help determine which component has an issue. In addition, you can test the components with the commands in Testing the CASP System.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. provides the Status API that returns the health of the components. You can run this command to help determine which component has an issue. In addition, you can test the components with the commands in Testing the CASP System.
Lost Phone, Damaged Bot, or Employee Replacement
There are several similar situations that have similar recovery procedures:
- Lost phone - one of the participants in your quorum
 One or more groups, comprised of participants group loses their phone. This participant
One or more groups, comprised of participants group loses their phone. This participant A member of any of the quorum groups. gets a new phone and needs to be reactivated by the remaining participants.
A member of any of the quorum groups. gets a new phone and needs to be reactivated by the remaining participants. - Employee replacement or a damaged bot - an employee who is a participant
 A member of any of the quorum groups. in your quorum
A member of any of the quorum groups. in your quorum One or more groups, comprised of participants group either switches positions or leaves the company. Alternatively, you have a bot that gets damaged. This participant
One or more groups, comprised of participants group either switches positions or leaves the company. Alternatively, you have a bot that gets damaged. This participant A member of any of the quorum groups. now needs to be replaced in the quorum
A member of any of the quorum groups. now needs to be replaced in the quorum One or more groups, comprised of participants.
One or more groups, comprised of participants.
The CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vault implementation has built-in support for these scenarios. For a lost phone, the participant
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vault implementation has built-in support for these scenarios. For a lost phone, the participant![]() A member of any of the quorum groups. can just be reactivated. To replace a participant
A member of any of the quorum groups. can just be reactivated. To replace a participant![]() A member of any of the quorum groups., deactivate the current participant
A member of any of the quorum groups., deactivate the current participant![]() A member of any of the quorum groups. from the relevant vault and then add the replacement participant
A member of any of the quorum groups. from the relevant vault and then add the replacement participant![]() A member of any of the quorum groups. to the vault.
A member of any of the quorum groups. to the vault.
These actions are part of the regular operations supported by CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vaults and do not require any specific disaster recovery protocol. For details about adding participants to an existing vault, deactivating participants, and reactivating participants, refer to the Participant Flows.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vaults and do not require any specific disaster recovery protocol. For details about adding participants to an existing vault, deactivating participants, and reactivating participants, refer to the Participant Flows.
CORE Loss
Run the Status API to determine if there is a problem with the CORE. This API returns the health of the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. components.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. components.
If a CORE server or cluster is lost or destroyed, you can bring up a new set of servers and then restore from your backups. See the CORE Restore Procedure.
After restoring, rerun the Status API to determine all components are healthy.
CASP Server Loss
If the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. server (i.e., the CASP
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. server (i.e., the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. Orchestrator) holding your CASP
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. Orchestrator) holding your CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vaults is lost, you can install new CASP
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. vaults is lost, you can install new CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. server. If you saved the casp.conf configuration file, copy it to the new server. If not, recreate the casp.conf file using the parameters for the existing CORE and database.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. server. If you saved the casp.conf configuration file, copy it to the new server. If not, recreate the casp.conf file using the parameters for the existing CORE and database.
After restoring, rerun the Status API to determine all components are healthy.
CASP Database Loss
Run the Status API to determine if there is a problem with the database. This API returns the health of the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. components.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. components.
If the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. database is lost, you can use the methods described by each database vendor to restore the CASP
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. database is lost, you can use the methods described by each database vendor to restore the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. backup:
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. backup:
After restoring, rerun the Status API to determine all components are healthy.
Total System Loss
In case of a total loss of the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. system, including CASP
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. system, including CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions., CORE, and the database, the private keys in vault can still be recovered if you have the cold backup key and the vault backup.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions., CORE, and the database, the private keys in vault can still be recovered if you have the cold backup key and the vault backup.
The previous methods are for restoring CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. components for recovery of the CASP
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. components for recovery of the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. system itself. However, there are cases where it is required to restore the actual vaults outside of at the CASP
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. system itself. However, there are cases where it is required to restore the actual vaults outside of at the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. system, such as in a standalone compatible wallet.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. system, such as in a standalone compatible wallet.
Other use cases include:
- An exchange system where the customer
 The entity that initially holds the crypto asset and requests storage in the crypto asset vault. wants to be able to recover funds even if the exchange service ceases to operate. For this case, it can store the backup data in a different location and the backup key in a safe location outside of the exchange system.
The entity that initially holds the crypto asset and requests storage in the crypto asset vault. wants to be able to recover funds even if the exchange service ceases to operate. For this case, it can store the backup data in a different location and the backup key in a safe location outside of the exchange system. - Moving from CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. to a different vault system.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. to a different vault system.
Using this approach requires the following steps:
- Set up the backup keys during CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. installation (see Prepare Vault Key Recovery).
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. installation (see Prepare Vault Key Recovery). - Get the backup data per generated vault and sub-account.
- Verify the backup information using the
verifyoption of the CASP Restore Utility. This option allows you to verify backup data integrity without decrypting the vault key. - Use the backup data along with the private key to retrieve the original seed/key using the
restoreoption of the CASP Restore Utility.
CASP Restore Utility
Unbound CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. includes
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. includes casp_restore utility that enables verification of the encrypted vault key backup and reconstruction of the vault key. This utility is installed by the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. RPM
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. RPM![]() File format for software package distributed by RPM Package Manager (and is also available as a separate download).
File format for software package distributed by RPM Package Manager (and is also available as a separate download).
The casp_restore runs on these platforms:
- RHEL/CentOS 7.2 and later
- Ubuntu 16.04
It uses the following parameters:
- The vault key backup file (see Backup the vault key).
- Two PEM
 Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" files with RSA keys that were in use when the vault was created
Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" files with RSA keys that were in use when the vault was created - A file with the vault key public key.
The utility is called with the following command line:
casp_restore [options]
It has these options:
-op <restore|verify>- Specify the required operation: restore or verify.-alg <algorithm of the vault key>- Specify the algorithm associated with the vault key: eddsa Edwards-curve Digital Signature Algorithm, ecdsa, or tots.
Edwards-curve Digital Signature Algorithm, ecdsa, or tots.-in <file>- the name of the backup file that includes the encrypted key-vault and its metadata.-rsa1 <pem-file>- For the
verifyoption - the PEM Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" file with the public RSA key specified by the
Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" file with the public RSA key specified by the --key_1option in theekm_set_offline_backup_keys.shscript. - For the
restoreoption - the PEM Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" file with the corresponding private RSA key.
Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" file with the corresponding private RSA key. - -rsa1-pwd <password> -optional password if the file is password-protected.
- For the
-rsa2 <pem-file>- For the
verifyoption - the PEM Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" file with the public RSA key specified by the
Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" file with the public RSA key specified by the --key_2option in theekm_set_offline_backup_keys.shscript. - For the
restoreoption - the PEM Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" file with the corresponding private RSA key.
Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" file with the corresponding private RSA key. - -rsa2-pwd <password> - optional password if the file is password-protected.
- For the
-public-key <file>- Specify the vault key public key. This file contains the public-key value in the-in <file>.-out <PEM- Applicable in the Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" file with the decrypted key>
Base64 encoded DER wrapped by "--- BEGIN <type> ---" and "--- END <type> ----" file with the decrypted key>-oprestorecase.- -out-pwd <password> - optional password to protect the
-out <file>.
- -out-pwd <password> - optional password to protect the
The verify option is applicable for -alg eddsa or ![]() Edwards-curve Digital Signature Algorithm
Edwards-curve Digital Signature Algorithm-alg ecdsa cases.
Note
This utility is backward compatible with backups created using a single RSA key before version 2.0.2112. To restore such backups, omit the -rsa2 parameter and its password
Master Key Extractor
Note
This script only works for Bitcoin. For other wallets, please contact Unbound Support.
A Python script, called Master Key Extractor, is provided along with the CASP![]() Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. Restore utility. Master Key Extractor creates a BIP32 master key from a .pem file. The .pem file is the output of the CASP Restore Utility.
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. Restore utility. Master Key Extractor creates a BIP32 master key from a .pem file. The .pem file is the output of the CASP Restore Utility.
The script is called with the following command line:
masterkey_extractor.py [options]
The script has these options:
- -p (or --pem) - Private key .pem file. The file must not be in PKCS
 Public-Key Cryptography Standards - Industry-standard cryptography specifications. #8 format.
Public-Key Cryptography Standards - Industry-standard cryptography specifications. #8 format. - -l (or --level) - Derivation level.
- -c (or --cpar) - cpar, chain code of the parent key.
- -n (or --childnumber) - Child number.
- -f (or --parentfingerprint) - Parent fingerprint.
- -t (or --testnet) - For testnet instead of mainnet.
The output of the script is a master key (in xprv format), like so:
abcd1234ABCD5678Z1CeAh2pKFwY8JLjVQDXUoFQwMbAuUgYCtFnyA9jwFixgUJRRBVsVQ\
AGK4VcXBHjBsWhqGhiuLQXj9habcd1234ABCD5678
The string includes the private key and other derivation information that was provided to the script. It can be used by other wallets to derive the keys that have actual funds associated with them.
Restore Examples
Restore a Deterministic (non-BIP) Vault
The following steps show an example of restoring a deterministic![]() Calculation that each time results in the same value vault.
Calculation that each time results in the same value vault.
- For this example, we use these parameters:
- CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. server URL: 192.168.0.149
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. server URL: 192.168.0.149 - Vault ID: 381ab347-0e18-4bdf-8a7f-7f02332e655f
- Name of the file containing the private key: casp_backup_private.pem
- Coin type: Bitcoin Testnet
- CASP
- Get the backup data.
- Save the contents (without the quotes) of the received backupData field to a file, called backupData.txt.
- Get the public key.
- Save the contents (without the quotes) of the received publicKey field to a file, called publicKey.txt.
- Run the CASP Restore Utility.
- Convert the received key into plain text.
- Run the Master Key Extractor.
curl --request GET \
--url http://192.168.0.149/casp/api/v1.0/mng/vaults/381ab347-0e18-4bdf-8a7f-7f02332e655f/backup \
--header 'authorization: Bearer b3JpOjJkOTMyNGYzLTM0MjItNDgwNC1hYTkyLWY5ZThlYWExNmRmYw=='
Response:
{
"vaultID": "381ab347-0e18-4bdf-8a7f-7f02332e655f",
"backupData": "ZWNiYWNrMDEAgALKAQAQ"
}
Note
The backupData field has been truncated for example purposes.
curl --request GET \
--url http://192.168.0.149/casp/api/v1.0/mng/vaults/381ab347-0e18-4bdf-8a7f-7f02332e655f/publickey \
--header 'authorization: Bearer b3JpOjJkOTMyNGYzLTM0MjItNDgwNC1hYTkyLWY5ZThlYWExNmRmYw=='
Response:
{
"publicKey": "3056301006072A8648CE3D020106052B8104000A03420004D40671DD6DB05B96721BF8\
54EF56E7EDD9FC10B4CED0090F365740513CFDE7A8691C6CA4ACBE307B0BCFBFF6F56397\
D2C015AD6C437CB2482DFA019DF23657D6"
}
/opt/casp/bin/casp_restore -op restore -alg ecdsa -in backupData.txt -rsa casp_backup_private.pem -public-key publicKey.txt -out ec-key
openssl ec -in ec-key -outform PEM -out restored.plain.pem
python /tmp/masterkey_extractor.py -p restored.plain.pem --testnet
You now have the master key (in WIF format), which is a string that includes the private key that was provided to the script. It can be used by other wallets that have actual funds associated with them.
To restore your wallet, use the master key in Electrum:
- In Electrum, select File > New/Restore.
- Give the wallet a name and then click Next.
- Select Import Bitcoin addresses or private keys, and then click Next.
- Enter the master key, and then click Next.
A wallet is created using the master key.
Restore an HD (BIP44) Vault
The following steps show an example of restoring an HD![]() Hierarchical Deterministic - a type of deterministic Bitcoin wallet derived from a known seed, that allows for the creation of child keys from the parent key. Because the child key is generated from a known seed there is a relationship between the child and parent keys that is invisible to anyone without that seed. vault.
Hierarchical Deterministic - a type of deterministic Bitcoin wallet derived from a known seed, that allows for the creation of child keys from the parent key. Because the child key is generated from a known seed there is a relationship between the child and parent keys that is invisible to anyone without that seed. vault.
- For this example, we use these parameters:
- CASP
 Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. server URL: 192.168.0.166
Unbound’s Crypto Asset Security Platform (“CASP”) provides the advanced
technology and the architecture to secure crypto asset transactions. server URL: 192.168.0.166 - Vault ID: db15bb8d-baec-4ceb-858c-7ae967261933
- Name of the file containing the private key: casp_backup_private.pem
- Sub-account number: 0
Coin type: Bitcoin Testnet
- CASP
- Get the backup data.
- Save the contents (without the quotes) of the received backupData field to a file, called backupData.txt.
- Save the contents (without the quotes) of the received publicKey field to a file, called publicKey.txt.
- Run the CASP Restore Utility.
- Convert the received key into plain text.
- Run the Master Key Extractor. The parameters are from the response of the backup curl command.
curl --request GET \
--url http://192.168.0.166/casp/api/v1.0/mng/vaults/db15bb8d-baec-4ceb-858c-7ae967261933/coins/1/accounts/0/backup
Response:
{
"backupData": "ZWNiYWNrMDEAgALKAQAIAAACAo+aT5hBI2WZiNvmLR8dr4pe/MJ",
"bipLevel": 3,
"cpar": "772FB73BF97DF1E7E1A8BA6BC3F9656D8A633DF9873C0C2DBAC2003C65A6A652",
"parentFingerprint": "2039A9A5",
"childNumber": 0,
"publicKey": "3056301006072A8648CE3D020106052B8104000A03420004E7A1172F667C3923C6C40AC\
A03E392457820B0F7CE144007919F4363BCF978EAE51188C10287A8E6FE211CFBB7166B09\
47AAB56324635AC60C0009296F28EC64"
}
Note
The backupData field has been truncated for example purposes.
/opt/casp/bin/casp_restore -op restore -alg ecdsa -in backupData.txt -rsa casp_backup_private.pem -public-key publicKey.txt -out ec-key
openssl ec -in ec-key -outform PEM -out restored.plain.pem
python /tmp/masterkey_extractor.py -p restored.plain.pem \
-l 3 \
-c 772FB73BF97DF1E7E1A8BA6BC3F9656D8A633DF9873C0C2DBAC2003C65A6A652 \
-n 0 \
-f 2039A9A5 \
--testnet
You now have the master key (in xprv/tprv format), which is a string that includes the private key and other derivation information that was provided to the script. It can be used by other wallets to derive the keys that have actual funds associated with them.
To restore your wallet, use the master key in Electrum:
- In Electrum, select File > New/Restore.
- Give the wallet a name and then click Next.
- Select Standard wallet, and then click Next.
- Select Use a master key, and then click Next.
- Enter the master key, and then click Next.
A BIP wallet is created using the master key.