Requirements
CORE Server Requirements
Hardware
- CPU:
- X86 2.0 GHz 64-bit (Intel, AMD) 3rd or later generation.
- IBM Z 15.
- RAM: 4 GB.
- Disk space: 200 MB.
Server OS
- Windows 2012 64 bit, Windows 2016, and Windows 2019
- RH
 Red Hat Linux 7.2, 7.7, 7.9, and 8.1, 8.4
Red Hat Linux 7.2, 7.7, 7.9, and 8.1, 8.4 - Ubuntu 16.04, 18.04, 20.04
- Debian 9 and 10
- Amazon Linux 2
Note
For Debian 9, OpenSSL 1.1.0 is required, and for Debian 10, OpenSSL 1.1.1 is required.
Notes:
- Intel/AMD CPU must provide
AES, SSSE3, PCLMULDQ,andRDRANDinstructions. These instructions are available starting with the 3rd generation of processors. To check whether your processor meets these requirements: - Linux: Examine the flags property in the
/proc/cpuinfofile. - Windows: Download the Coreinfo utility and run
Coreinfo64.exe -f. - IBM Z 15 CPU running LinuxONE III OS is supported by CORE clients and servers. For platform-specific details see the “Running Unbound on the Z platform” guide.
Java Requirements
The CORE server software assumes that Java 8 GA or higher GA version is installed on the server.
CORE Client Requirements
CORE client is supported on X86 and POWER® processors.
Client Hardware
X86 Architecture
- CPU:
- X86 2.0 GHz 64-bit (Intel, AMD) 3rd or later generation. See note above.
- POWER® P7, P8, P9
- RAM: 2 GB.
- Disk space: 200 MB.
Client OS
- Windows 2008 R2 64 bit, 2102, 2016, and 2019
- Windows 7 64 bit and Windows 10
- RH
 Red Hat Linux 7.2, 7.6, 7.7, 7.9, and
RH
Red Hat Linux 7.2, 7.6, 7.7, 7.9, and
RH Red Hat Linux 8.1, 8.4
Red Hat Linux 8.1, 8.4
- Ubuntu 16.04, 18.04, and 20.04
- Debian 8, 9 and 10
- SuSE 12 SP2 and SuSE 15 SP1
- Amazon Linux 2
- Oracle Linux 7
- macOS 10.15 (Catalina) and 11 (Big Sur)
- AIX 7.2 32 bit
Note
For Debian 8 and 9, OpenSSL 1.1.0 is required, and for Debian 10, OpenSSL 1.1.1 is required.
Note
IBM Z 15 CPU running LinuxONE III OS is supported by CORE clients and servers. For platform-specific details see the “Running Unbound on the Z platform” guide.
OpenSSL Integration Requirements
To integrate OpenSSL based application with the Unbound libraries, see Integration with OpenSSL and use the following OpenSSL platforms:
- OpenSSL 1.0.2<x>
- OpenSSL 1.1.0<x>
- OpenSSL 1.1.1<x>
-
OpenSSL 1.1.1 is required when using TLS
 Transport Layer Security - a cryptographic protocol that provides communications security over a computer network 1.3.
Transport Layer Security - a cryptographic protocol that provides communications security over a computer network 1.3.
Note
gnuTLS - Configure CORE Client to use gnuTLS (see use_gnuTLS Setting) when it is integrated with applications that already utilize OpenSSL for SSL![]() Secure Sockets Layer - a cryptographic protocol that provides communications security over a computer network. communication. This requirement is specifically true (and so far, this is the only case we are aware of) with
Secure Sockets Layer - a cryptographic protocol that provides communications security over a computer network. communication. This requirement is specifically true (and so far, this is the only case we are aware of) with Oracle TDE support. ![]() Transparent Data Encryption - Technology to encrypt database files.
Transparent Data Encryption - Technology to encrypt database files.
Java Development Requirements
To integrate Java application with the Unbound Java classes, see Developing in Java and use the following Java distributions:
- Oracle:
- Java 8: Oracle Java 64-bit Standard Edition (SE) 8 u312 and later.
- Java 11: Oracle Java 64-bit Standard Edition (SE) 11.0.2 and later
- OpenJDK:
- Java 8: OpenJDK 1.8.0_262 and later.
- Java 11: OpenJDK 11.0.2 and later.
Note
CORE is compliant with OpenJDK builds that conform to the Java Technology Compatibility Kit (TCK). For potential candidates check OCTLA Signatories List. We recommend AdoptOpenJDK with the HotSpot JVM.
Cipher Suite Requirements
TLS1.2. The CORE servers use the following TLS1.2 HIGH+AESGCM cipher suites in their internal connections and expect the same from their clients:
- RSA:
- TLS
 Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048)
Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - TLS
 Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048)
Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048)
- TLS
- DHE:
- TLS
 Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_DHE_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048)
Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_DHE_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - TLS
 Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_DHE_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048)
Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_DHE_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048)
- TLS
- ECDHE:
- TLS
 Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1)
Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - TLS
 Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1)
Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1)
- TLS
TLS![]() Transport Layer Security - a cryptographic protocol that provides communications security over a computer network 1.3. In addition to mandating TLS1.2 compliance from its clients, CORE servers can be configured to use TLS1.3 protocol on platforms running JDK 11 with OpenSSL 1.1.1 or GnuTLS 3.6.3. CORE supports the following TLS1.3 cibersuites:
Transport Layer Security - a cryptographic protocol that provides communications security over a computer network 1.3. In addition to mandating TLS1.2 compliance from its clients, CORE servers can be configured to use TLS1.3 protocol on platforms running JDK 11 with OpenSSL 1.1.1 or GnuTLS 3.6.3. CORE supports the following TLS1.3 cibersuites:
- TLS
 Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_AES_128_GCM_SHA256
Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_AES_128_GCM_SHA256 - TLS
 Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_AES_256_GCM_SHA384
Transport Layer Security - a cryptographic protocol that provides communications security over a computer network_AES_256_GCM_SHA384
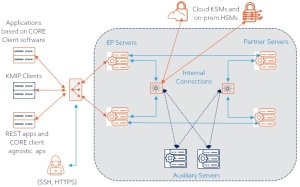
Connectivity Requirements
External connections to EPs provide complete management and service links. External connections to the other type of servers are intended for CLI![]() Command Line Interface-based maintenance and troubleshooting.
Command Line Interface-based maintenance and troubleshooting.
Internal connections among the servers are used to distribute management and MPC![]() Multiparty computation - A methodology for parties to jointly compute a function of their inputs while keeping those inputs private. commands.
Multiparty computation - A methodology for parties to jointly compute a function of their inputs while keeping those inputs private. commands.
External Connections
| Purpose | Port | From | To | Comment |
|---|---|---|---|---|
| Management Connection |
443 | Web browser | EP server | UI Management (EP server only) |
| 22 | Admin station | CORE Linux server | SSH |
|
| 3389 | Admin station | CORE Windows server | Remote desktop protocol (RDP) port |
Note
The CORE system is preconfigured to accept the service and UI requests on EP ports 443 and 8443. To use a different port, see Customize the Service Port.
Internal Connections
Internal connections serve CORE internal traffic planes:
- Control plane - using port 443.
- Data plane - using port 6603. In addition, port 6604 serves MPC
 Multiparty computation - A methodology for parties to jointly compute a function of their inputs while keeping those inputs private. computations performed in the FIPS mode
Multiparty computation - A methodology for parties to jointly compute a function of their inputs while keeping those inputs private. computations performed in the FIPS mode UKC system mode that allows processing FIPS-certified and not-certified keys.
UKC system mode that allows processing FIPS-certified and not-certified keys.
CORE cluster establishes the following connections:
- An EP and its Partner are interconnected via 443, 6603 (MPC
 Multiparty computation - A methodology for parties to jointly compute a function of their inputs while keeping those inputs private.), and 6604 (for FIPS
Multiparty computation - A methodology for parties to jointly compute a function of their inputs while keeping those inputs private.), and 6604 (for FIPS Federal Information Processing Standards - standards developed by the United States federal government for use in computer systems by non-military government agencies and government contractors-mode MPC
Federal Information Processing Standards - standards developed by the United States federal government for use in computer systems by non-military government agencies and government contractors-mode MPC Multiparty computation - A methodology for parties to jointly compute a function of their inputs while keeping those inputs private.).
Multiparty computation - A methodology for parties to jointly compute a function of their inputs while keeping those inputs private.). - All EPs are interconnected via 443 port.
- All Partners are interconnected via 443 port.
- An Auxiliary server is connected to all EPs and Partners via 443,6603, and 6604 (for FIPS
 Federal Information Processing Standards - standards developed by the United States federal government for use in computer systems by non-military government agencies and government contractors-mode MPC
Federal Information Processing Standards - standards developed by the United States federal government for use in computer systems by non-military government agencies and government contractors-mode MPC Multiparty computation - A methodology for parties to jointly compute a function of their inputs while keeping those inputs private.).
Multiparty computation - A methodology for parties to jointly compute a function of their inputs while keeping those inputs private.).
In particular:
| Server | Port | To | Comment |
|---|---|---|---|
| EP | 443 | The assigned Partner | Internal Management connection |
| All other EPs | |||
| All Aux servers | |||
| 6603 | The assigned Partner | Crypto connection for non-FIPS |
|
| All Aux servers | |||
| 6604 | The assigned Partner | Crypto connection for the FIPS mode |
|
| All Aux servers |
| Server | Port | To | Comment |
|---|---|---|---|
| Partner | 443 | The assigned EP | Internal Management connection |
| All other Partners | |||
| All Aux servers | |||
| 6603 | The assigned EP | Crypto connection for non-FIPS |
|
| All Aux servers | |||
| 6604 | The assigned EP | Crypto connection for the FIPS mode |
|
| All Aux servers |
| Server | Port | To | Comment |
|---|---|---|---|
| Auxiliary | 443 | All EP servers | Internal Management connection |
| All Partner servers | |||
| 6603 | All EP servers | Crypto connection for non-FIPS |
|
| All Partner servers | |||
| 6604 | All EP servers | Crypto connection for FIPS |
|
| All Partner servers |
Minimal Cluster Requirements
The minimal CORE system operating in the non-FIPS mode![]() UKC system advanced execution mode that hasn't yet received the FIPS certification is comprised of two servers: EP and its Partner. Starting with the CORE release 2.0.2010, an Auxiliary server is just an optional accelerator of the symmetric cryptography in the non-FIPS
UKC system advanced execution mode that hasn't yet received the FIPS certification is comprised of two servers: EP and its Partner. Starting with the CORE release 2.0.2010, an Auxiliary server is just an optional accelerator of the symmetric cryptography in the non-FIPS![]() Federal Information Processing Standards - standards developed by the United States federal government for use in computer systems by non-military government agencies and government contractors systems. For such systems we recommend the following:
Federal Information Processing Standards - standards developed by the United States federal government for use in computer systems by non-military government agencies and government contractors systems. For such systems we recommend the following:
-
New deployments: Start without the auxiliary server - bootstrap the EP-Partner pair. As needed, add an Auxiliary server to improve the symmetric key performance. However, if you plan an intensive use of the symmetric operations, bootstrap the server triplet from the start.
-
Upgrades: If the system does not use symmetric operations intensively - you can remove all Aux servers from the cluster.