AWS KMS Keys
Some notes about keys in AWS KMS![]() Key Management System:
Key Management System:
- Key names may include dash "-". Other special characters are forbidden.
- Data encrypted by an AES key can be decrypted only by the same key.
- Automatic key rotation does not apply to asymmetric KMS
 Key Management System keys or imported keys.
Key Management System keys or imported keys. - Only AES-256 keys can be imported.
AWS Key Types
The following table summarizes supported KMS![]() Key Management System key types and BYOK
Key Management System key types and BYOK![]() Bring Your Own Key/non-BYOK
Bring Your Own Key/non-BYOK![]() Bring Your Own Key key creation options.
Bring Your Own Key key creation options.
| Key type | Size/Curve | non-BYOK | BYOK |
|---|---|---|---|
| RSA | 2048, 3072, 4096 | √ | |
| ECC |
P256, P384, P521, SECP256K1 | √ | |
| AES | 128, 256 | √ | √ |
References:
AWS Key Crypto Operations and Algorithms
The following table summarizes UID-based crypto operations supported by AWS KMS![]() Key Management System.
Key Management System.
| Key type | Decrypt/Encrypt | Sign/Verify |
|---|---|---|
| RSA | √ | √ |
| ECC |
√ | |
| AES | √ |
References:
The following list summarizes KMS![]() Key Management System algorithms that can be used via CORE. Algorithms not supported by CORE are
Key Management System algorithms that can be used via CORE. Algorithms not supported by CORE are [shaded].
- RSA (RSA algorithms) for Keys 2K, 3K, 4K
-
- Decrypt
- OAEP
 Optimal Asymmetric Encryption Padding - A padding scheme often used together with RSA encryption of symmetric keys. with SHA1
Optimal Asymmetric Encryption Padding - A padding scheme often used together with RSA encryption of symmetric keys. with SHA1 - OAEP
 Optimal Asymmetric Encryption Padding - A padding scheme often used together with RSA encryption of symmetric keys. with SHA256
Optimal Asymmetric Encryption Padding - A padding scheme often used together with RSA encryption of symmetric keys. with SHA256 -
- Sign
- PSS
 probabilistic signature scheme. Abbreviation of RSASSA-PSS with SHA256, SHA384, and SHA512
probabilistic signature scheme. Abbreviation of RSASSA-PSS with SHA256, SHA384, and SHA512 - PKCS
 Public-Key Cryptography Standards - Industry-standard cryptography specifications.-V1_5 SHA256, SHA384, and SHA512
Public-Key Cryptography Standards - Industry-standard cryptography specifications.-V1_5 SHA256, SHA384, and SHA512 - ECC
 Elliptic-curve cryptography - an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields (EC algorithms) for P256, P384, P521,
Elliptic-curve cryptography - an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields (EC algorithms) for P256, P384, P521, -
- Sign
- ECDSA
 Elliptic Curve Digital Signature Algorithm - A variant of the Digital Signature Algorithm (DSA) which uses elliptic curve cryptography. with sha256,
sha384, sha512
Elliptic Curve Digital Signature Algorithm - A variant of the Digital Signature Algorithm (DSA) which uses elliptic curve cryptography. with sha256,
sha384, sha512
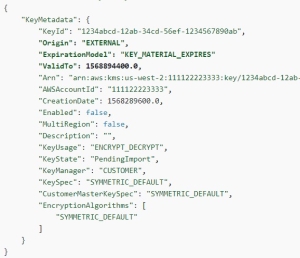
AWS Key Metadata
See Key Metadata.
To obtain also the multi-region information, use Describe Key.
AWS Key Management Operations
The following table compares CORE and KMS![]() Key Management System key management options and references KMS
Key Management System key management options and references KMS![]() Key Management System documentation for further details.
Key Management System documentation for further details.
| Operation | CORE | AWS | Comment | Reference |
|---|---|---|---|---|
| Generate | √ | √ | CreateKey | |
| Import | √ | √ |
|
|
| Key policy |
|
|
||
| Delete | √ | √ |
|
|
| Cancel Deletion | √ |
|
Cancel key deletion | |
|
Activate / Revoke |
√ |
|
||
| Enable | √ | √ |
|
|
| Disable | √ | √ | Disable Key | |
| Rekey / Rotate | √ | ≈ |
|
|
| Get Info | √ | √ |
|
Key Metadata |
| Get Public | √ | √ |
|
Get Public |
| Get Private | √ |
|
Note: the ≈ sign indicates the availability of alternatives