CORE Users
CORE user represents a person or an application that manages or uses elements of the CORE system.
Default Users
The first CORE user is the security officer (SO![]() Security officer - UKC partition administrator role.) of the first ("root") partition, also known as Root SO
Security officer - UKC partition administrator role.) of the first ("root") partition, also known as Root SO![]() Security officer - UKC partition administrator role.. Its password is specified during the CORE system bootstrap.
Security officer - UKC partition administrator role.. Its password is specified during the CORE system bootstrap.
Root SO![]() Security officer - UKC partition administrator role. may create additional SOs in the Root partition. It also creates all other CORE partitions. All such partitions are created with two persistent users named
Security officer - UKC partition administrator role. may create additional SOs in the Root partition. It also creates all other CORE partitions. All such partitions are created with two persistent users named so and user:
so- This user manages the partition.
- Its password is assigned during the partition's creation.
- It may join any other user group (see User Group) to obtain additional privileges reserved to the members of the group.
user- By default, it is a passwordless user that serves applications integrated with CORE Client libraries and are authenticated using the client certificate.
- By default, it is granted unrestricted management and use of crypto material in the partition.
- It cannot join any user group.
The settings of CORE user include:
- Name
- Alias (for a user that represents an SSO
 Single Sign-On user)
Single Sign-On user) - Role
- Status (user is locked or active)
- Dates of events in its life
- Membership in User Groups
Note
Membership in a User Group is granted or denied by managing the User Group's members. See User Groups Tab.
Managed Users
CORE supports the following options to manage its users:
- SSO
 Single Sign-On (OpenID Connect) authentication - credentials are managed and validated by an OIDC
Single Sign-On (OpenID Connect) authentication - credentials are managed and validated by an OIDC OpenID Connect is identity layer on top of the OAuth 2.0 protocol provider. CORE uses the user's personal information (such as email address) provided by the OIDC
OpenID Connect is identity layer on top of the OAuth 2.0 protocol provider. CORE uses the user's personal information (such as email address) provided by the OIDC OpenID Connect is identity layer on top of the OAuth 2.0 protocol Provider to match the authenticated user with its CORE partition and permissions. Regular expressions may be used to match groups of users.
OpenID Connect is identity layer on top of the OAuth 2.0 protocol Provider to match the authenticated user with its CORE partition and permissions. Regular expressions may be used to match groups of users. - Native authentication - credentials are managed and validated by CORE.
- LDAP
 Lightweight Directory Access Protocol authentication - credentials are managed and validated by an LDAP
Lightweight Directory Access Protocol authentication - credentials are managed and validated by an LDAP Lightweight Directory Access Protocol provider. The second factor, if applied, is verified by the CORE.
Lightweight Directory Access Protocol provider. The second factor, if applied, is verified by the CORE.
Management of SSO User
The permissions of a user authenticated by an OIDC![]() OpenID Connect is identity layer on top of the OAuth 2.0 protocol provider are set indirectly by managing one of the following:
OpenID Connect is identity layer on top of the OAuth 2.0 protocol provider are set indirectly by managing one of the following:
- A CORE user group(s) that the user is a member of.
- A native user that acts as its representative (alias) in the partition.
An SSO![]() Single Sign-On user is granted all permissions that are granted to its group or alias.
Single Sign-On user is granted all permissions that are granted to its group or alias.
- User create
- An SSO
 Single Sign-On user is associated with its partition and permissions using the following methods:
Single Sign-On user is associated with its partition and permissions using the following methods: -
- Specifying the SSO
 Single Sign-On user's PI in a partition's User Group. See User Groups Tab.
Single Sign-On user's PI in a partition's User Group. See User Groups Tab. - Specifying the SSO
 Single Sign-On user's PI in the settings of a partition's native user. See Create an SSO-user.
Single Sign-On user's PI in the settings of a partition's native user. See Create an SSO-user.
- Specifying the SSO
- User modify
- To modify permissions of an SSO
 Single Sign-On user, Edit permissions of its base or move it to a different base.
Single Sign-On user, Edit permissions of its base or move it to a different base. - User show
- To show permissions of an SSO
 Single Sign-On user, use the Show command of its base.
Single Sign-On user, use the Show command of its base. - User delete
- Delete the user's PI from its base.
Management of Native User
Users authenticated by CORE are called native users. Native CORE users are created and managed by the partition's SO![]() Security officer - UKC partition administrator role..
Security officer - UKC partition administrator role..
Notes
1. The first (default) users of a partition (so and user) are persistent. They can not be deleted.
2. For better security, in the CORE Client Stack applications, reassign the default user to a role with the least permissions required for executing crypto commands without user credentials.
- User create
- To create a native user, specify its credentials and role. See ucl user create.
- User password modify
- To change self-password, use ucl user change-pwd.
- To reset the other user's password, use ucl user reset-pwd.
- In extreme cases, the Root SO
 Security officer - UKC partition administrator role. can change the password of any user in any partition by using the ucl user recover-pwd command.
Security officer - UKC partition administrator role. can change the password of any user in any partition by using the ucl user recover-pwd command. - User role modify
- UCL
 Unbound Command Language: to modify a user's role using UCL
Unbound Command Language: to modify a user's role using UCL Unbound Command Language, delete the username and create it again with the required role.
Unbound Command Language, delete the username and create it again with the required role. - UI: you can use Change Role. In addition, you may change user's membership in user groups.
- User group
- The initial specification of a user's role may be expanded by adding the user to User Group(s). In such a case, the user is granted with all permissions associated with the group(s).
- This capability applies to all users except the default
user. - User show
- To check the user's settings and status, use the ucl user show command in UCL
 Unbound Command Language or use Show Permissions in UI.
Unbound Command Language or use Show Permissions in UI. - User delete
- To delete any other user except the default USER and SO
 Security officer - UKC partition administrator role., use the ucl user delete command.
Security officer - UKC partition administrator role., use the ucl user delete command.
Management of LDAP User
In CORE , the user authenticated by LDAP![]() Lightweight Directory Access Protocol is managed as a native user apart from its password management.
Lightweight Directory Access Protocol is managed as a native user apart from its password management.
CORE User Authentication
CORE user authentication involves:
- Validation of Credentials.
- Validation of the 2nd authentication factor (2FA
 Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password)) which, in certain cases, can be optionally bypassed. See The 2nd Factor Validation Options.
Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password)) which, in certain cases, can be optionally bypassed. See The 2nd Factor Validation Options.
Validation of Credentials
Every CORE service request must go along with credentials of the user or the CORE Users that is exchanged for the user credentials or for the OIDC![]() OpenID Connect is identity layer on top of the OAuth 2.0 protocol Access Token.
OpenID Connect is identity layer on top of the OAuth 2.0 protocol Access Token.
The credentials of the default CORE users are validated by CORE. The credentials of the managed CORE users may be validated by CORE , OIDC![]() OpenID Connect is identity layer on top of the OAuth 2.0 protocol or LDAP
OpenID Connect is identity layer on top of the OAuth 2.0 protocol or LDAP![]() Lightweight Directory Access Protocol providers.
Lightweight Directory Access Protocol providers.
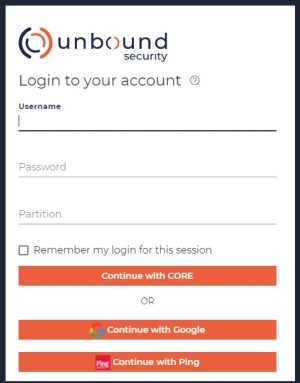
The following UI login page capture shows an example of CORE and OIDC![]() OpenID Connect is identity layer on top of the OAuth 2.0 protocol validation options presented to user in a particular system. For further login details, see UI Sign-in.
OpenID Connect is identity layer on top of the OAuth 2.0 protocol validation options presented to user in a particular system. For further login details, see UI Sign-in.
Note
To manage OIDC![]() OpenID Connect is identity layer on top of the OAuth 2.0 protocol providers in CORE , see OIDC Provider Management in CORE and here about integrating CORE with various OIDC
OpenID Connect is identity layer on top of the OAuth 2.0 protocol providers in CORE , see OIDC Provider Management in CORE and here about integrating CORE with various OIDC![]() OpenID Connect is identity layer on top of the OAuth 2.0 protocol providers.
OpenID Connect is identity layer on top of the OAuth 2.0 protocol providers.
Credentials Validation by OIDC Provider
Validation of a user credentials that has selected the "Continue with <OIDC![]() OpenID Connect is identity layer on top of the OAuth 2.0 protocol provider>" option is carried by the selected provider. A user may skip specifying the required partition. In such a case, CORE shall scan all partitions, collect all the partitions where the user is defined and select one of them as the initial login partition. The user could roam from there to any other of the collected partitions. See SSO User about managing such users.
OpenID Connect is identity layer on top of the OAuth 2.0 protocol provider>" option is carried by the selected provider. A user may skip specifying the required partition. In such a case, CORE shall scan all partitions, collect all the partitions where the user is defined and select one of them as the initial login partition. The user could roam from there to any other of the collected partitions. See SSO User about managing such users.
Credentials Validation by CORE
Validation of a user credentials that has selected the "Continue with CORE" option is performed by the CORE server. CORE imposes the following username and password requirements:
- Username is
- Case-insensitive. It is displayed in lowercase characters.
- Unique in the partition.
- May contain characters that are specified in Username Permitted Characters.
- Password complexity requirements are
- Specified by the partition settings. See Password Requirement.
Credentials Validation by LDAP Provider
Validation of a user credentials is delegated to the LDAP![]() Lightweight Directory Access Protocol provider. The LDAP
Lightweight Directory Access Protocol provider. The LDAP![]() Lightweight Directory Access Protocol-authenticated user must be defined in CORE using the same username as used by the LDAP
Lightweight Directory Access Protocol-authenticated user must be defined in CORE using the same username as used by the LDAP![]() Lightweight Directory Access Protocol provider. The user's password is defined and managed by the LDAP
Lightweight Directory Access Protocol provider. The user's password is defined and managed by the LDAP![]() Lightweight Directory Access Protocol provider only. See LDAP Provider Settings.
Lightweight Directory Access Protocol provider only. See LDAP Provider Settings.
Using CORE Access Token for Authentication
The CORE access token is JWT![]() JSON Web Token - means of representing claims transferred between two parties token issued by UNBOUND in exchange for the valid credentials or for the valid OIDC
JSON Web Token - means of representing claims transferred between two parties token issued by UNBOUND in exchange for the valid credentials or for the valid OIDC![]() OpenID Connect is identity layer on top of the OAuth 2.0 protocol Access token. It includes the following data:
OpenID Connect is identity layer on top of the OAuth 2.0 protocol Access token. It includes the following data:
- partitions
- A partition (or set of partitions) that this token is applicable with indication of the role assigned to the token's holder.
- For example,
"partitions": {"test": ["so"]}specifies that the token is applicable intestpartition only and it grants its holder the permissions ofSOrole. Security officer - UKC partition administrator role.
Security officer - UKC partition administrator role. - sub
- Subject - full user name. A full user name combines user name with the partition name. For example,
SOfrom partition Security officer - UKC partition administrator role.
Security officer - UKC partition administrator role.testis specifiedso@test. - orig
- Origin - IP address to whom this token has been provided.
- iss
- Issuer - The issuer (and the signer) of the token. Must be UNBOUND.
- other JWT
 JSON Web Token - means of representing claims transferred between two parties data
JSON Web Token - means of representing claims transferred between two parties data - See example below
Example of a decoded payload section of a token:
{
"partitions": {"test": ["so"]},
"sub": "so@test",
"orig": "172.31.0.238",
"iss": "UNBOUND",
"is_refresh": false,
"use_ephemeral": false,
"exp": 1629134010,
"iat": 1629132210,
"jti": "d0c569a7-aaa3-4e7c-8a0c-26a2ed53b407"
}
Note that token already contains the full user name (<user>@<partition> in the "sub" field.
Obtaining CORE Token
To exchange the user credentials for the CORE JWT![]() JSON Web Token - means of representing claims transferred between two parties access token, use Get OAuth authentication token API with the following data:
JSON Web Token - means of representing claims transferred between two parties access token, use Get OAuth authentication token API with the following data:
'grant_type=password'
'username=<username>@<partition-name>'
'password=<user password>
If the TOTP![]() Time-based One Time Password 2nd authentication factor is required, add the following to the above parameters:
Time-based One Time Password 2nd authentication factor is required, add the following to the above parameters:
'otp=<TOTP code>'
Note
Username is full name. It specifies the username and the partition name.
Using CORE Token
- In CORE REST
 Representational State Transfer (REST) - an architectural style that defines a set of constraints and properties based on HTTP. Web Services that conform to the REST architectural style, or RESTful web services, provide interoperability between computer systems on the Internet. API, use the JWT
Representational State Transfer (REST) - an architectural style that defines a set of constraints and properties based on HTTP. Web Services that conform to the REST architectural style, or RESTful web services, provide interoperability between computer systems on the Internet. API, use the JWT JSON Web Token - means of representing claims transferred between two parties token in
JSON Web Token - means of representing claims transferred between two parties token inAuthorization: Bearer <JWT. JSON Web Token - means of representing claims transferred between two parties token>
JSON Web Token - means of representing claims transferred between two parties token> - In UCL
 Unbound Command Language commands, the Base64 value of a token is specified as the
Unbound Command Language commands, the Base64 value of a token is specified as the --password (-w)value.
-w {\"token\":\"<JWT access token in Base64>\"}
For example:
ucl sign-code --file C:\tmp\test.exe -n my-sign-key \
-w {\"token\":\"eyJraWQiOiI..... TRUNCATED.....sZyI6IkVP83pNd0A\"}
Note
The --user option must be omitted (the user's full name is included in the token).
The 2nd Factor Validation Options
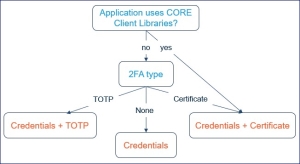
CORE enforces validation of the 2nd authentication factor unless specifically configured to avoid such validation in the selected partitions. By design:
- The certificate-based 2FA
 Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password) is enforced on all applications that use the CORE Client libraries.
Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password) is enforced on all applications that use the CORE Client libraries. - For the other applications, once the user credentials have been validated (either externally or by CORE ), the validation of the 2nd authentication factor is applied unless configured otherwise. CORE provides the following 2nd factor options that may be selected by a partition SO
 Security officer - UKC partition administrator role.:
Security officer - UKC partition administrator role.: - Certificate. This is the default option. The 2nd factor is a certificate installed on the client's machine. See Client Types and Certificates.
- TOTP
 Time-based One Time Password code. The 2nd factor is TOTP
Time-based One Time Password code. The 2nd factor is TOTP Time-based One Time Password code obtained by the user from its personal Authenticator application such as Google Authenticator. See TOTP-based 2FA.
Time-based One Time Password code obtained by the user from its personal Authenticator application such as Google Authenticator. See TOTP-based 2FA. - (None. The 2nd authentication factor is not required.)
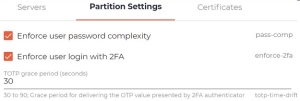
The following settings govern the selection of the required option:
- System setting: No-cert.
- Partition settings: default-client and
enforce-2fa(see TOTP Settings).
This table summarizes the 2FA![]() Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password) selection in a partition based on these settings.
Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password) selection in a partition based on these settings.
| setting | default value | Configurable options | |||
|---|---|---|---|---|---|
|
no-cert |
0 | 0 | 1 | 1 | |
|
default-client |
1 | 0 | 0 | 1 | |
| enforce-2fa | 0 | * | * | 0 | 1 |
| 2FA |
Certificate | None | TOTP |
||
TOTP-based 2FA
Introduction
In the TOTP![]() Time-based One Time Password-based 2FA
Time-based One Time Password-based 2FA![]() Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password), the 2nd factor is the proof that the user has access to the device where she installed the secret provided to her during the TOTP
Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password), the 2nd factor is the proof that the user has access to the device where she installed the secret provided to her during the TOTP![]() Time-based One Time Password service enrollment. The proof doesn't disclose the secret and it becomes irrelevant after 60 to 120 seconds (based on the configuration).
Time-based One Time Password service enrollment. The proof doesn't disclose the secret and it becomes irrelevant after 60 to 120 seconds (based on the configuration).
TOTP![]() Time-based One Time Password uses the following components:
Time-based One Time Password uses the following components:
- Secret.
- UTC time-step.
- Grace period.
The secret that TOTP![]() Time-based One Time Password validator provides to user upon her enrollment into TOTP
Time-based One Time Password validator provides to user upon her enrollment into TOTP![]() Time-based One Time Password service. This secret is unique per username@partitonname. The user uploads the secret and its metadata to the designated TOTP
Time-based One Time Password service. This secret is unique per username@partitonname. The user uploads the secret and its metadata to the designated TOTP![]() Time-based One Time Password generator device whose clock is synchronized with the TOTP
Time-based One Time Password generator device whose clock is synchronized with the TOTP![]() Time-based One Time Password validator clock. See User Enrollment .
Time-based One Time Password validator clock. See User Enrollment .
The UTC time is divided into fixed intervals (e.g., 30 secs). The length of the interval used by the TOTP![]() Time-based One Time Password validator is shared with the TOTP
Time-based One Time Password validator is shared with the TOTP![]() Time-based One Time Password generator on the user's device. UTC time is normalized by this interval becoming a counter (time-step) of UTC time intervals on both sides.
Time-based One Time Password generator on the user's device. UTC time is normalized by this interval becoming a counter (time-step) of UTC time intervals on both sides.
To allow the OTP![]() One-Time Password (or Pin) - a password that is valid for only one login session or transaction. message propagation and processing delays, the validator shall compare the received OTP
One-Time Password (or Pin) - a password that is valid for only one login session or transaction. message propagation and processing delays, the validator shall compare the received OTP![]() One-Time Password (or Pin) - a password that is valid for only one login session or transaction. code with the codes that could be created in the previous time-steps based on the configuration (30 to 90 seconds resulting into up to 3 time-steps).
One-Time Password (or Pin) - a password that is valid for only one login session or transaction. code with the codes that could be created in the previous time-steps based on the configuration (30 to 90 seconds resulting into up to 3 time-steps).
The OTP![]() One-Time Password (or Pin) - a password that is valid for only one login session or transaction. code is the cryptographic derivative of user's unique secret and the current time-step. The TOTP
One-Time Password (or Pin) - a password that is valid for only one login session or transaction. code is the cryptographic derivative of user's unique secret and the current time-step. The TOTP![]() Time-based One Time Password generator on user's device refresh this code every 30 secondsl.
Time-based One Time Password generator on user's device refresh this code every 30 secondsl.
CORE Implementation of TOTP
Setup
To enforce the TOTP![]() Time-based One Time Password code as the 2nd authentication factor for CORE partition user, the partition SO
Time-based One Time Password code as the 2nd authentication factor for CORE partition user, the partition SO![]() Security officer - UKC partition administrator role. must make the following preparations:
Security officer - UKC partition administrator role. must make the following preparations:
- Make sure that the system-wide Certificate-based 2FA
 Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password) is disabled. See No-cert setting.
Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password) is disabled. See No-cert setting. - Make sure that the default-client in the partition is enabled. See default-client.
- Enable
enforce-2fa(see TOTP Settings). See Partition Settings in UI. As needed, extend the grace period (default - one time-step of 30 secs)
User Enrollment
To start using TOTP![]() Time-based One Time Password, user must register with the TOTP
Time-based One Time Password, user must register with the TOTP![]() Time-based One Time Password validator, obtain and install the shared secret.
Time-based One Time Password validator, obtain and install the shared secret.
Prerequisites:
- The partition settings as specified in Setup.
- The user had not yet enrolled to TOTP
 Time-based One Time Password-based 2FA
Time-based One Time Password-based 2FA Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password) or her previous enrollment has been reset, see User TOTP 2FA Maintenance.
Two-factor authentication - Authentication method that requires both something a user has (for example, a certificate) and something the user knows (for example, a password) or her previous enrollment has been reset, see User TOTP 2FA Maintenance.
Procedure:
- User logins using UI by providing her credentials.
- CORE validates the credentials and creates user-specific secret.
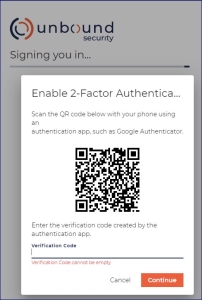
- CORE UI :
- Presents the secret and the associated metadata (e.g. Issuer of the secret and user name) in the QR format.
- Prompts the user to provide the OTP
 One-Time Password (or Pin) - a password that is valid for only one login session or transaction. code that will be displayed to her once she adds the new TOTP
One-Time Password (or Pin) - a password that is valid for only one login session or transaction. code that will be displayed to her once she adds the new TOTP Time-based One Time Password consumer to her TOTP
Time-based One Time Password consumer to her TOTP Time-based One Time Password generator (Google Authenticator).
Time-based One Time Password generator (Google Authenticator). - User opens Google Authenticator and scans the QR code.
- A new TOTP
 Time-based One Time Password application appears in the Google Authenticator.
Time-based One Time Password application appears in the Google Authenticator. - User enters the OTP
 One-Time Password (or Pin) - a password that is valid for only one login session or transaction. code requested in step#2 to complete the enrollment.
One-Time Password (or Pin) - a password that is valid for only one login session or transaction. code requested in step#2 to complete the enrollment.
For example,
encodes the OTP![]() One-Time Password (or Pin) - a password that is valid for only one login session or transaction. URI for so@test:
One-Time Password (or Pin) - a password that is valid for only one login session or transaction. URI for so@test:
otpauth://totp/so%40test?\
secret=RZHKXNMA7OMQECFG7IJ7RX7Q6JQNTE6H&\
issuer=Unbound%20Security
For example, in the case of the above QR code, the Authenticator shows
Unbound Security (so@test)
<ephemeral OTP code>
User Login
User login is 2 step procedure:
- Provide credentials in the targeted partition.
- When prompted, provide the currently displayed OTP
 One-Time Password (or Pin) - a password that is valid for only one login session or transaction. code.
One-Time Password (or Pin) - a password that is valid for only one login session or transaction. code.
User TOTP 2FA Maintenance
CORE provides the following options to force user's re-enrollment into TOTP![]() Time-based One Time Password service:
Time-based One Time Password service:
- A partition SO
 Security officer - UKC partition administrator role. can enforce re-enrollment of any other user in the partition. See Reset 2-Factor Authentication command, but it cannot re-enroll itself. If there are no other SOs in the partition, only the Root SO
Security officer - UKC partition administrator role. can enforce re-enrollment of any other user in the partition. See Reset 2-Factor Authentication command, but it cannot re-enroll itself. If there are no other SOs in the partition, only the Root SO Security officer - UKC partition administrator role. can re-enroll it.
Security officer - UKC partition administrator role. can re-enroll it. - The Root SO
 Security officer - UKC partition administrator role. can re-enroll any SO
Security officer - UKC partition administrator role. can re-enroll any SO Security officer - UKC partition administrator role. in any partition. See Reset SO Password. This command also resets its password.
Security officer - UKC partition administrator role. in any partition. See Reset SO Password. This command also resets its password. - The Root SO
 Security officer - UKC partition administrator role. can also re-enroll itself by using the Reset 2-Factor Authentication command.
Security officer - UKC partition administrator role. can also re-enroll itself by using the Reset 2-Factor Authentication command. - Finally, when the Root SO
 Security officer - UKC partition administrator role. is locked out of the Root partition, it may be re-enrolled by the System Admin using the
Security officer - UKC partition administrator role. is locked out of the Root partition, it may be re-enrolled by the System Admin using the ekm_recover_root_so_pwdscript.